Implementing Authentication in Service Mesh: A Skeleton Outline
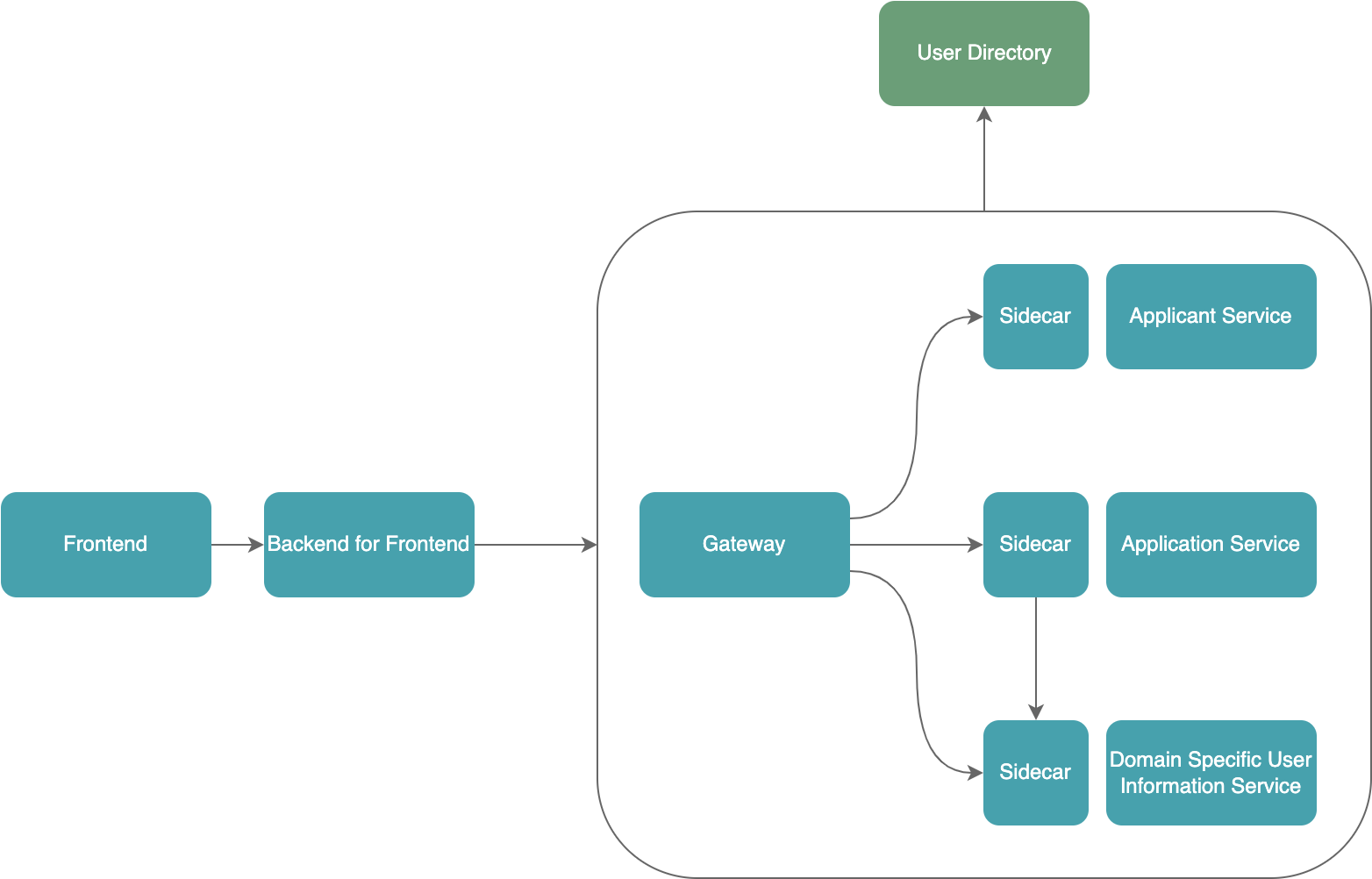
Authentication in a service mesh is a critical aspect of ensuring the security and integrity of your microservices architecture. In this guide, we will explore the process of setting up authentication in a service mesh, and specifically, we will delve into the advantages of implementing authentication. The entire architecture will be discussed, highlighting the use of OAuth2-proxy for the BFF (Backend for Frontend), Istio-gateway for the Gateway, and a custom OIDC (OpenID Connect) provider implemented using the Spring Authorization Server.
Bird eye: The whole architecture
Setting Up Authentication in Service Mesh
OAuth2-Proxy for BFF:
For the BFF layer, we leverage OAuth2-proxy as a robust solution for authentication. OAuth2-proxy acts as an intermediary between your application and OAuth2 providers, facilitating secure user authentication. It handles user sign-ins, token validation, and provides a seamless integration with various identity providers.
Istio-Gateway for Gateway Authentication:
At the Gateway layer, we employ Istio-gateway, which utilizes Envoy under the hood. Istio-gateway plays a pivotal role in managing external and internal traffic within the service mesh. It provides a unified and secure entry point for incoming requests, allowing for the enforcement of authentication policies and routing rules.
Custom OIDC Provider using Spring Authorization Server:
To implement the OIDC provider, we have opted for a custom solution using the Spring Authorization Server. This choice allows for a tailored and flexible OpenID Connect implementation, aligning with specific business requirements. The Spring Authorization Server acts as the identity provider, responsible for issuing and validating tokens, and handling user authentication.
Advantages of Authentication in Service Mesh
Enhanced Security:
Authentication in a service mesh adds an additional layer of security to your microservices architecture. By ensuring that only authorized users and services can interact with your application, you mitigate the risk of unauthorized access and potential security breaches.
Centralized User Management:
With a service mesh providing authentication, user management becomes centralized. This centralized approach simplifies the task of maintaining user credentials, roles, and permissions. It also streamlines the onboarding and offboarding processes, ensuring efficient and secure user access management.
Seamless Integration with External Systems:
Authentication mechanisms in the service mesh enable seamless integration with external systems, such as OAuth2 providers. This facilitates Single Sign-On (SSO) capabilities, allowing users to access multiple services with a single set of credentials, enhancing user experience and reducing the friction of authentication.
Policy Enforcement and Access Control:
Service mesh authentication enables the enforcement of access control policies at the gateway level. This ensures that only authenticated and authorized traffic is allowed to reach the microservices within the mesh. Fine-grained access control provides a granular approach to managing data privacy and service interaction.
Conclusion
Implementing authentication in a service mesh is a crucial step in building a secure and scalable microservices architecture. By leveraging tools like OAuth2-proxy, Istio-gateway, and custom OIDC providers such as the Spring Authorization Server, you can establish a robust authentication framework. The advantages of enhanced security, centralized user management, seamless integration, and access control policies contribute to a resilient and reliable service mesh infrastructure.